| tags: [ development git scm Amazon ] categories: [Development ]
Git Amazon
To finish off my posts on git and SSH, this time I will walk through configuring Amazon Code Commit as a remote repository for my small ‘MyNewCode’ git repository.
Configuring Amazon Code Commit for git
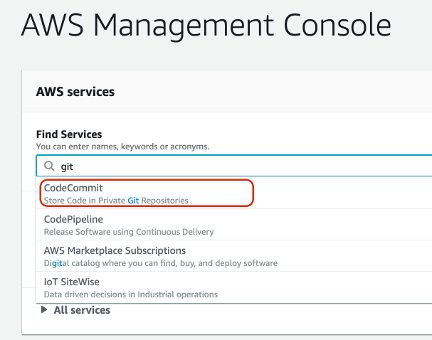
Locating Amazons' git repository offering can be found pretty quickly from the search field on the console.
Create Repository
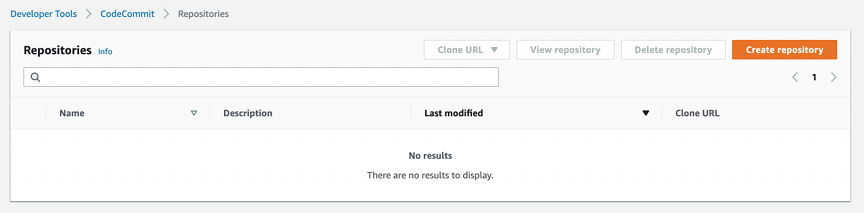
Creating a repository is straight forward. Press the ‘Create Repository’ button and fill in the initial details for the repository.
After creating the repository, I am directed to a page showing how to configure git for HTTPS. Although not what I want, it’s nice to see that they put detailed connection information up where it is most likely going to be needed.
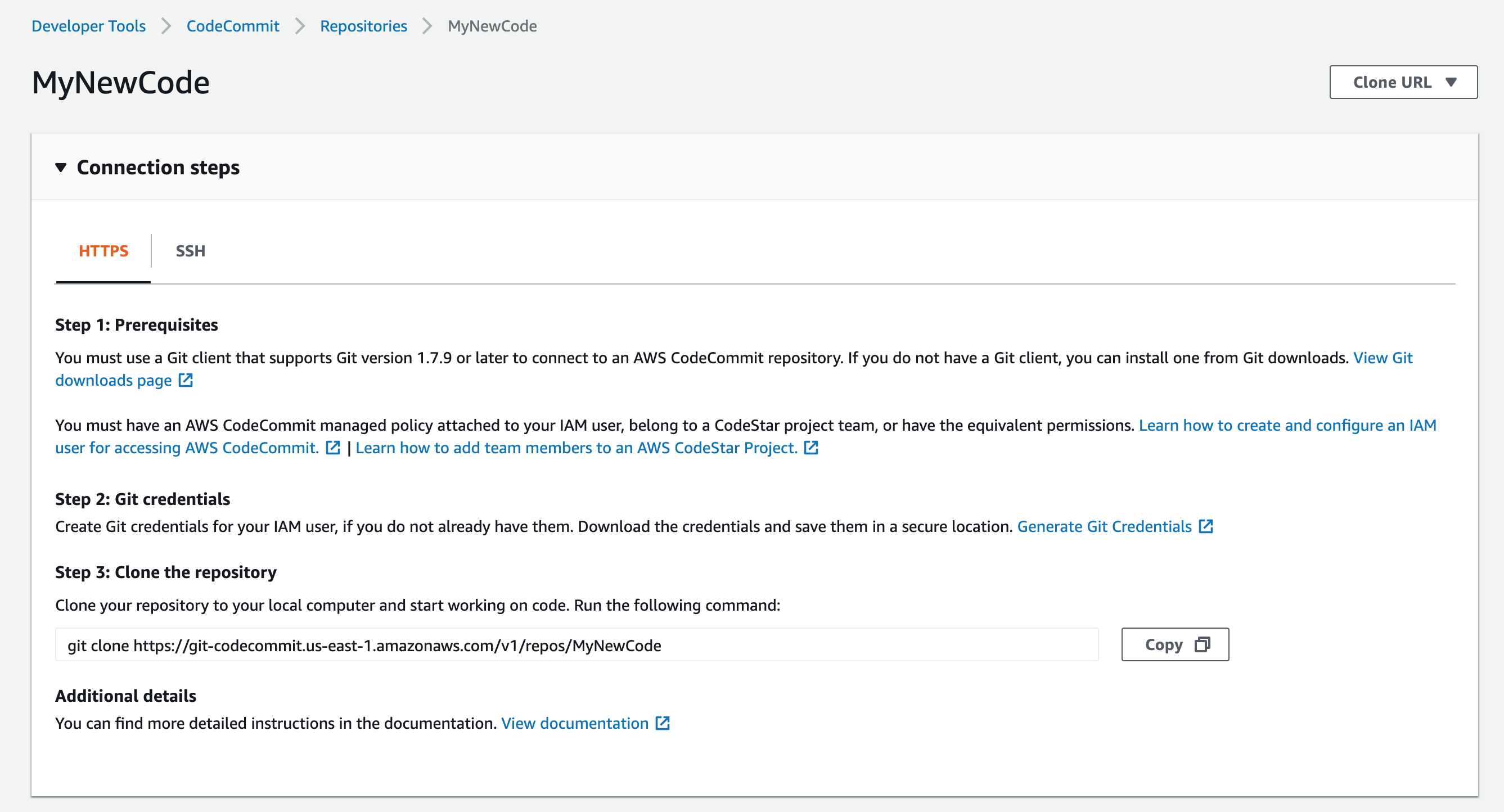
Hey, there’s a tab on the page to flip over to see information for ssh configuration.
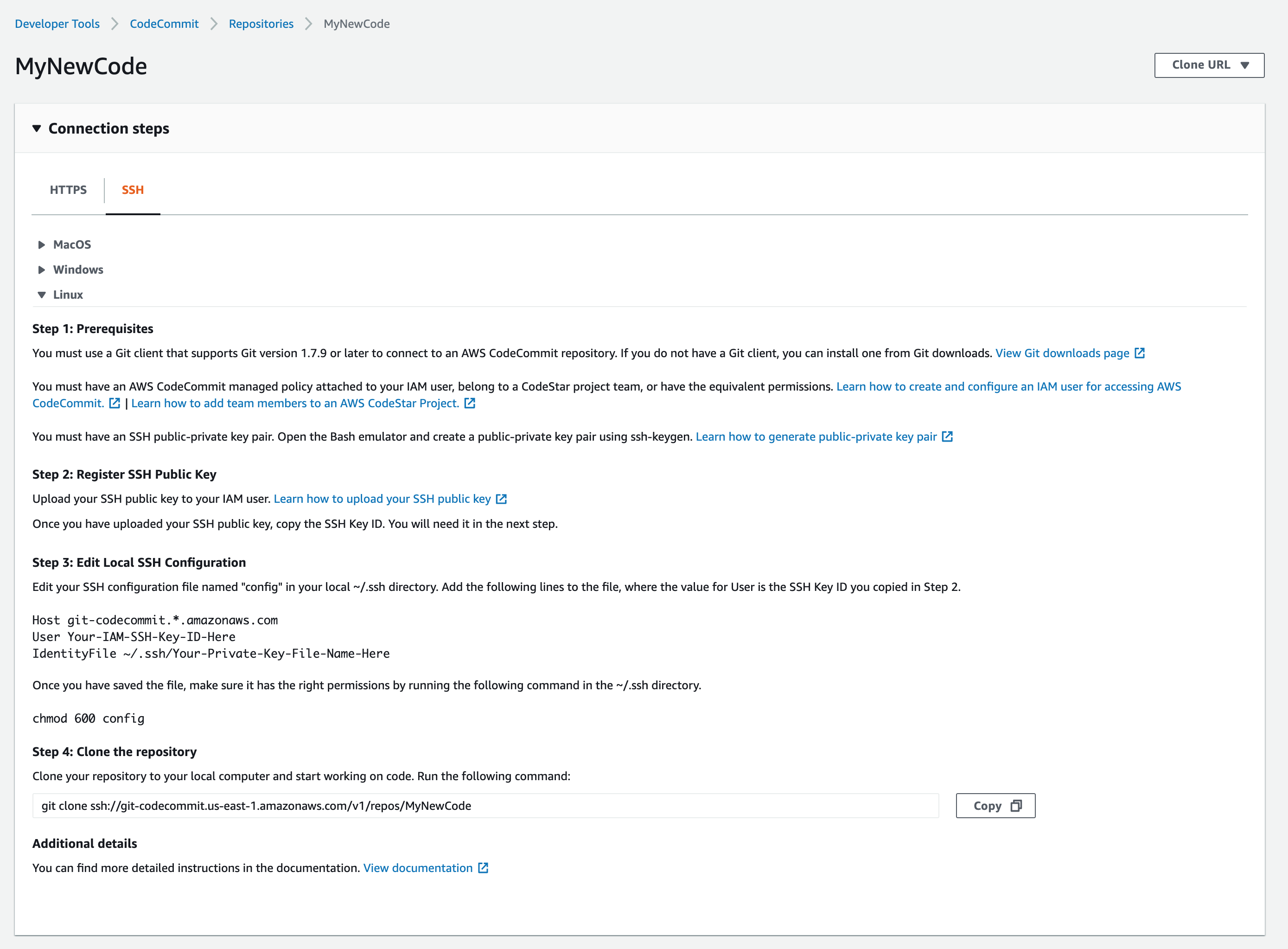
The instructions for SSH are pretty reasonable and similar to those described in Git Google. There is also a link to a very helpful ssh configuration document: Setup Steps for SSH Connections to AWS CodeCommit Repositories on Linux, macOS, or Unix Both the details on this page as well as the help document are needed to get the configuration working. I read through this supplemental document several times in order to get the connection to work as I wanted. I would highly recommend reading it if you’re going to try this out.
The directions shown here assume that I will start code development by cloning this repository. They don’t appear to provide directions on how to push an existing repository. Fortunately I have done this before.
Authorize use of Code Commit
In AWS, the user that will be doing git actions must be authorized to
interact with Code Commit. This is done through IAM by granting the
user the policy AWSCodeCommitFullAccess. To grant a policy, I had
to login as a user with elevated permissions that is allowed to assign
the policy. This is usually done by an administrator role.

After applying the policy, I returned to the user screen screen which
should show the AWSCodeCommitFullAccess policy is attached to the
user.

Create SSH Keys
Another nuance between Google and Amazon. In the Google case, the public ssh key was associated with the project. However in the Amazon environment, the public SSH key is associated with the user.
I still need a public/private ssh key pair to proceed. Like I did in the case of Git Google, I like to start with a unique ssh key pair. The AWS help documentation also recommends this approach.
$ ssh-keygen -f $HOME/.ssh/amazon_code_commit_repositories
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
...
Now that I’ve got a public and private key pair, I need to supply the public key to the Amazon user that will be performing git operations.
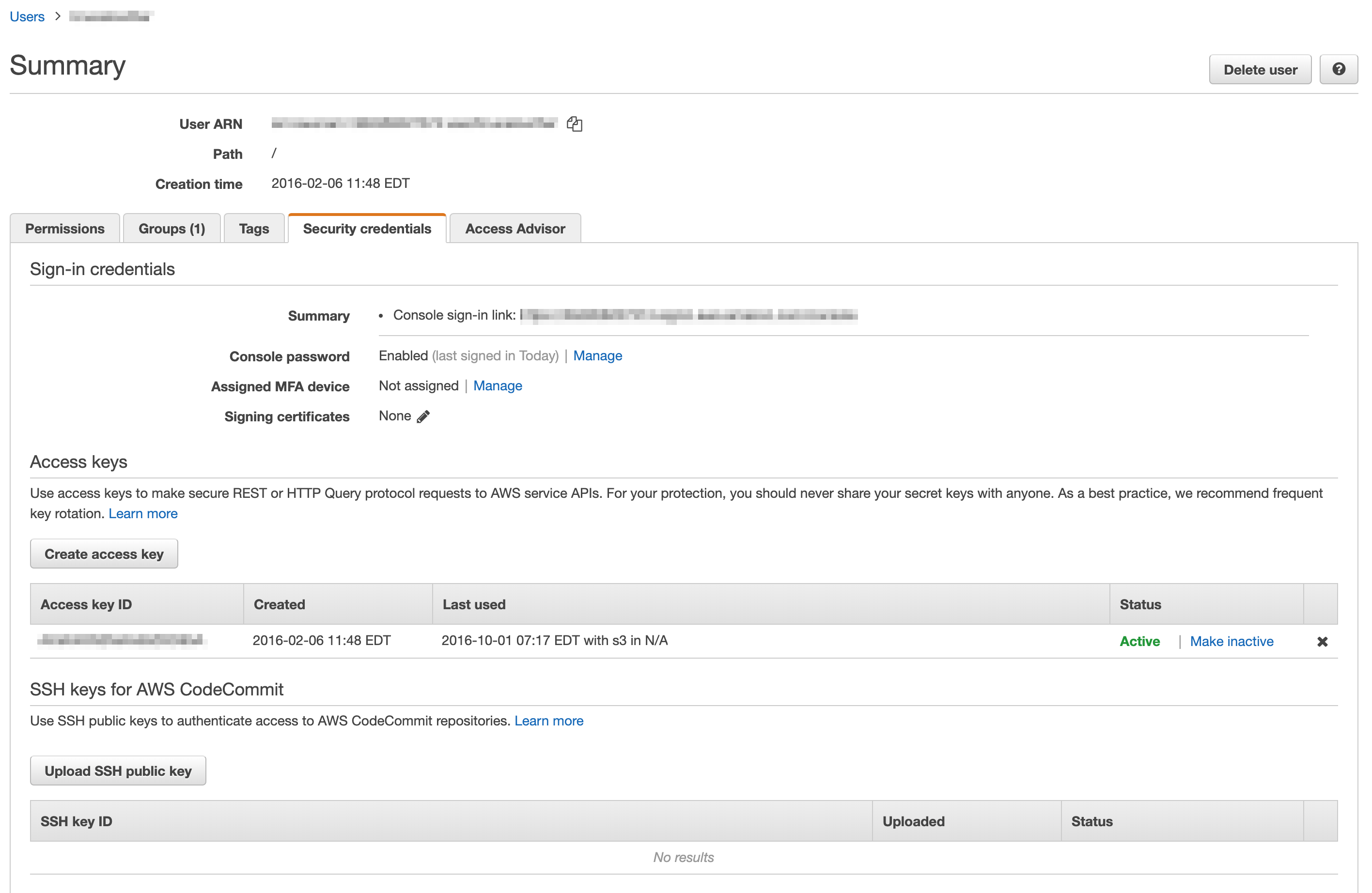
Grant SSH Permission
In IAM as a user with elevated privileges, I navigate to the user that will perform git operations. I open the Security Credentials pane and near the bottom of this screen capture, you can see the section for ‘SSH keys for AWS CodeCommit’.
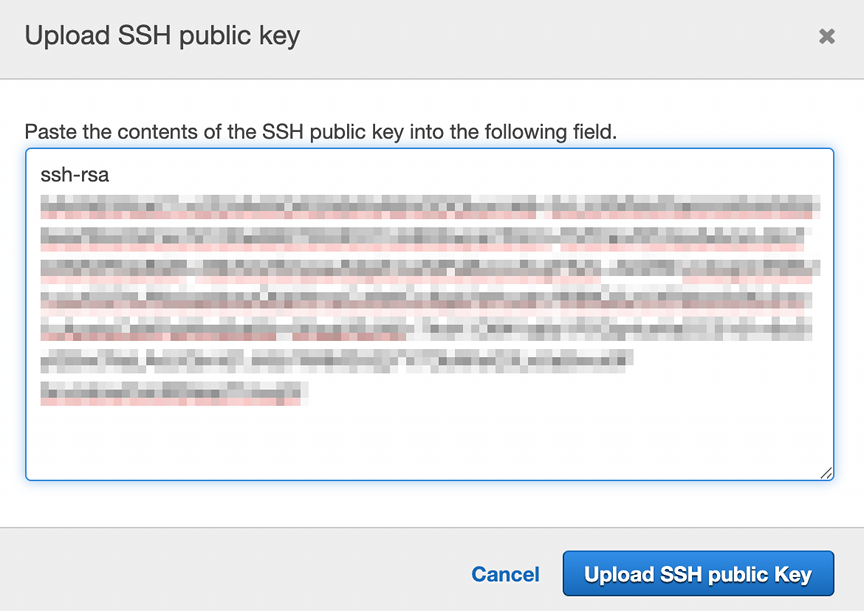
Pressing the ‘Upload SSH Public key’ button will pop up a simple
dialog to supply the contents of the public key file. As I’ve done
before, cat out the amazon_code_commit_repositories.pub file and
copy the entire contents into the field and press OK.
Configure $HOME/.ssh/config
The Setup Steps for SSH Connections to AWS CodeCommit Repositories on Linux, macOS, or Unix document is critical in this step as there are some nuances in the configuration that caused me some problems. Steps 7 and 8 specifically are new to me.
I added a section to the $HOME/.ssh/config file as before in
the google example, but in the Amazon case, there is a User
attribute added that is derived from adding the public ssh key to the
user.
Host git-codecommit.*.amazonaws.com
User FAKEFAKEFAKEFAKEJFYYHUFI
IdentityFile ~/.ssh/amazon_code_commit_repositories⏎
The User attribute is populated in the SSH Key ID field when the ssh
public key is added to the user. This appears to be some kind of hash
of the user and the SSH public Key. Fortunately it’s well documented!
See the following screen capture. There is a red oval identifying the
SSH key ID field.
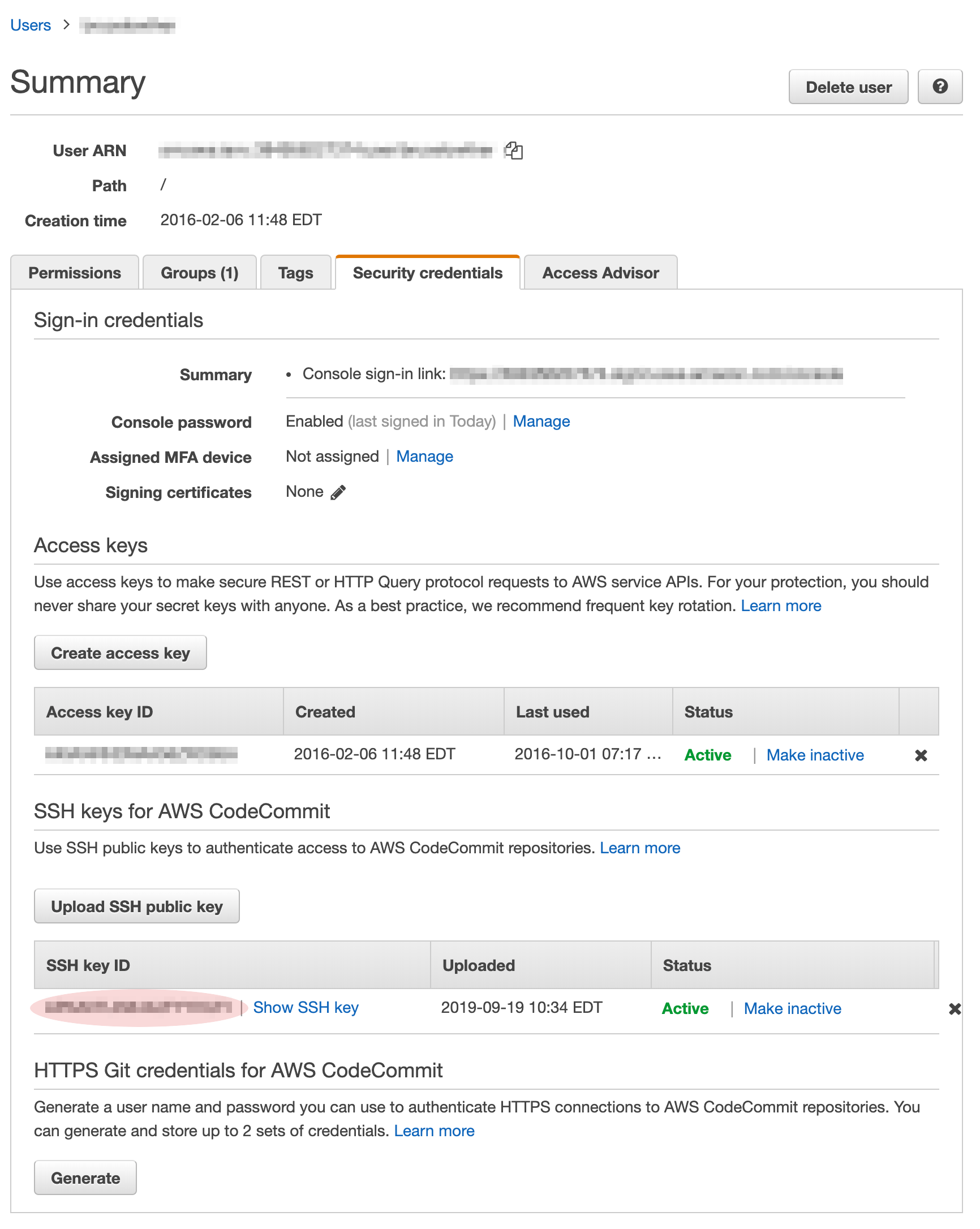
I initially assumed that the User attribute was the
IAM username however on a push I received the following error:
$ git push --all amazon
The authenticity of host 'git-codecommit.us-east-1.amazonaws.com
(52.94.288.146)' can't be established.
RSA key fingerprint is
SHA256:eLMY1j0DKA4uvDZcl/KgtFAKEANwX6t8+8isFAKEBoY.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added
'git-codecommit.us-east-1.amazonaws.com,52.94.288.146' (RSA) to the
list of known hosts.
sign_and_send_pubkey: signing failed: agent refused operation
Permission denied (publickey).
fatal: Could not read from remote repository.
Please make sure you have the correct access rights
and the repository exists.
So in the end I had to go back through the document and review steps 7 & 8 to get this right.
Adding an Amazon Remote
Now that all the ssh configuration has been taken care of, I added an additional remote to my local git repository.
$ cd /tmp/MyNewCode/
$ git remote -v
google ssh://someuser@gmail.com@source.developers.google.com:2022/p/googleproject-1234/r/MyNewCode (fetch)
google ssh://someuser@gmail.com@source.developers.google.com:2022/p/googleproject-1234/r/MyNewCode (push)
origin ssh://someuser@somehost:/home/someuser/GitSharedRepo/MyNewCode.git (fetch)
origin ssh://someuser@somehost:/home/someuser/GitSharedRepo/MyNewCode.git (push)
$ git remote add amazon ssh://git-codecommit.us-east-1.amazonaws.com/v1/repos/MyNewCode
$ git remote -v
amazon ssh://git-codecommit.us-east-1.amazonaws.com/v1/repos/MyNewCode (fetch)
amazon ssh://git-codecommit.us-east-1.amazonaws.com/v1/repos/MyNewCode (push)
google ssh://someuser@gmail.com@source.developers.google.com:2022/p/googleproject-1234/r/MyNewCode (fetch)
google ssh://someuser@gmail.com@source.developers.google.com:2022/p/googleproject-1234/r/MyNewCode (push)
origin ssh://someuser@somehost:/home/someuser/GitSharedRepo/MyNewCode.git (fetch)
origin ssh://someuser@somehost:/home/someuser/GitSharedRepo/MyNewCode.git (push)
Pushing to Amazon
$ git push --all amazon
Warning: Permanently added the RSA host key for IP address
'52.94.229.29' to the list of known hosts.
Counting objects: 6, done.
Delta compression using up to 4 threads.
Compressing objects: 100% (2/2), done.
Writing objects: 100% (6/6), 457 bytes | 0 bytes/s, done.
Total 6 (delta 0), reused 6 (delta 0)
To ssh://git-codecommit.us-east-1.amazonaws.com/v1/repos/MyNewCode
* [new branch] master -> master
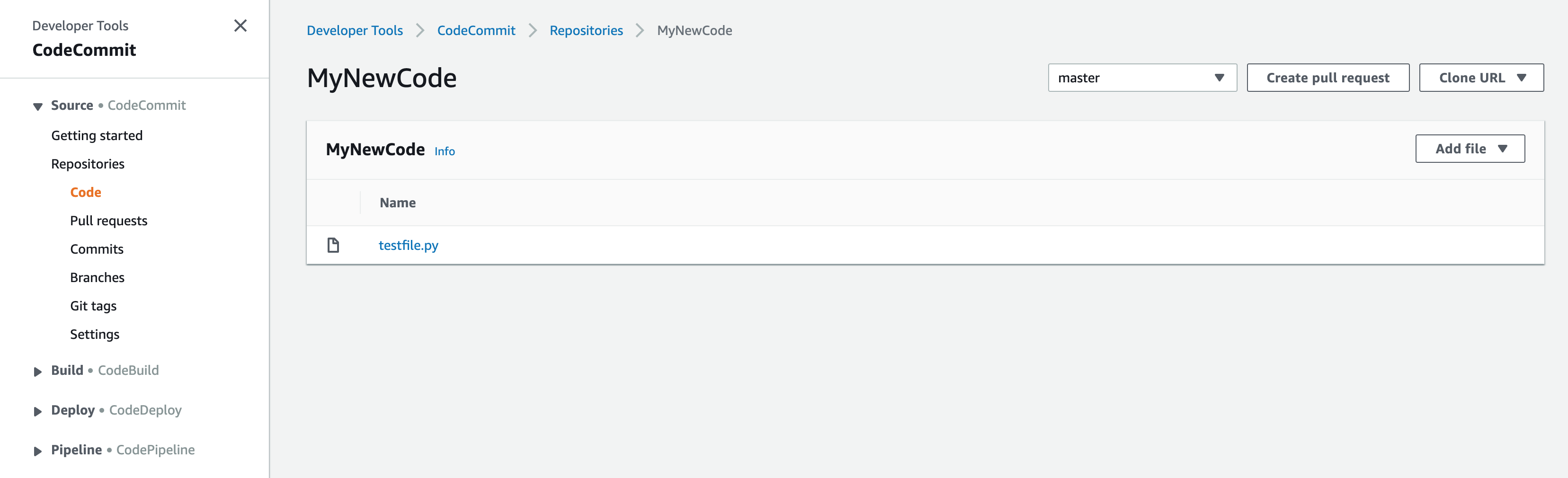
Amazon CodeCommit User Interface
Finally, I verified that I could see the git repository was visible from the CodeCommit user interface.
Where from here
Well that is all for now. Now that I know the option exists, I will look around for some code to bulk upload many repositories to GCP. If no code is out there, then I guess I’ll get to write it myself!
Also an outstanding item for future investigation is the cost of pushing all my repositories up. The pricing for both AWS and GCP seem to indicate that I would still be within the ‘Free’ zone with my frequency of changes (not very frequent) and the fact that there is only one of me with permission to these repositories.
I guess time will tell.
